WLAN security Basics | Security in Wireless LAN (WLAN),Wifi securities
This page on WLAN security basics covers security methods used in Wireless LAN (WLAN) network. This wifi security describes security mechanisms, WEP protocol, RC-4 encryption algorithm used in Wireless LAN (WLAN) network.
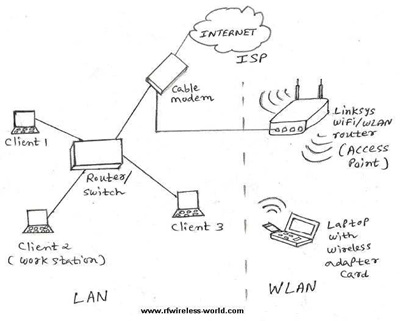
Figure below depicts the WLAN part integrated with LAN system components. As shown WLAN system composed of Station and Access Point. Access point helps interface wireless local area network devices with fixed LAN devices. Wireless network is more vulnerable to hacking compare to wired one. Hence more security is provided to the wireless portion and not to the wired one. This wifi security is very essential for the wifi users accessing the wifi network at public places such as restaurants, airports, railway stations etc.
WLAN has many benefits such as user mobility, rapid installation, flexibility and scalability. The WLAN security services are provided by WEP protocol (Wired Equivalent Privacy protocol). This protocol protects link level data during wireless transmissions between the stations(i.e. STAs/clients) and APs(Access Points). WEP protocol takes care of security only in the wireless part and not in the wired part.
There are three security services specified by IEEE for WLAN network viz. authentication, confidentiality and integrity.
Authentication takes care of denying the access for the stations who do not authenticate with the APs.
Confidentiality makes sure to prevent unauthorized entry into the WLAN network. Integrity makes sure that messages in the transit are not altered.
There are two authentication types defined in WLAN system(IEEE 802.11). They are open system authentication and shared key authentication. In open system authentication stations are allowed to join the WLAN network without any identity verification. It does use any cryptography or encryption algorithm. The other type shared key authentication uses RC4 cryptographic algorithm as explained below.
RC4 WLAN security algorithm

Following messages are exchanged between Station(STA or Client) and Access Point in shared key authenication. • Authentication Request: From STA to AP
• Challenge: AP generates random number and send it to STA.
• Response: STA using cryptographic key which is shared with AP encrypts this challenge and send it to the AP.
• Confirm Success:AP decrypts the result sent by the STA and allows access of the WLAN network provided the decrypted value matches with the random challenge transmitted initially.

The WEP protocol is explained in the figure-3 above. As shown Initialization Vector(IV) is added with shared key to form the encryption key. IV length is about 24 bits. Encryption key is of length from 40 bits to 104 bits. For 128 bit encryption algorithm, 104-bit WEP key is used which when added with 24 bit IV will become 128 bit size. This encryption key is XORedwith payload information which generated the ciphertext to be transmitted. Before modulo-2 , payload data is appended with CRC value of 32 bits which adds in error detection.
WiFi securities | Checklist to protect WiFi or WLAN Network
以下是支持WiFi证券清单tect the WLAN network or make the wifi network secured:
• Change the administrator password and username regularly.
• Turn the WEP Encryption ON
• Enable firewall on each PCs and routers
• Diable the auto connect feature • Turn off power of router or AP when they are not in the use
• Assign static IP addresses to the devices and keep it safe
• Disable broadcast of the SSID
• Enable MAC address filtering
Other than this page on Wireless LAN security i.e. WAN security (wifi security) one can refer following links on wireless security aspects in other wireless systems which include 2G(GSM), 3G(UMTS), 4G(LTE), Z-wave, Zigbee etc. One can also refer WLAN basic tutorial (11a, 11b), 11ac & 11ad tutorial and so on to know more.
Wireless security Related Links
3G SecurityLTE SecurityGSM SecurityZigbee SecurityZ-wave SecurityWeb App. SecurityBluetooth securityWiFi security
WLAN RELATED LINKS
WLAN 802.11ac Tutorial802.11ad TutorialWLAN tutorial802.11b basics11a Physical LayerDifference between 11a 11b 11g 11n